
TOP SECRET: Operation Social Selection
SUBJECT: The Limits of Target Acquisition Based on Social Connectivity
EXECUTIVE SUMMARY:
Due to advancements in data mining and personal connections (primarily leveraged from platforms like Facebook and Instagram), modern warfare tactics have shifted. We can now only hurt or neutralize personnel we “know” (i.e., those with a digital footprint intersecting ours). This presents unique challenges, as anonymity effectively creates immunity.
OBJECTIVE:
To neutralize threats efficiently by relying on the extensive (and often unwilling) cooperation of social media networks, because, let’s face it—if they don’t appear in our feed, they’re practically invisible.
SZIGORÚAN TITKOS: Social Selection Hadművelet
TÁRGY: A célpont-azonosítás korlátai a közösségi kapcsolatok alapján
VEZETŐI ÖSSZEFOGLALÓ:
Az adatbányászat és a személyes kapcsolati hálók fejlődése (elsősorban a Facebook és az Instagram platformjain keresztül) következtében a modern hadviselési taktikák átalakultak. Ma már csak azokat a személyeket tudjuk megsebezni vagy semlegesíteni, akiket „ismerünk” (azaz akiknek digitális jelenléte metszi a miénket). Ez egyedi kihívásokat teremt, mivel az anonimitás gyakorlatilag mentességet biztosít.
CÉLKITŰZÉS:
A fenyegetések hatékony semlegesítése a közösségi hálózatok kiterjedt (és gyakran nem önkéntes) együttműködésére támaszkodva, mert lássuk be — ha nem jelennek meg a hírfolyamunkban, gyakorlatilag láthatatlanok.

🇬🇧 English
Police state:
A country or political system in which the government uses the police, surveillance, and strict control to limit people’s freedom, often without respecting human rights or the rule of law.
🇪🇸 Spanish
Estado policial:
Un país o sistema político en el que el gobierno utiliza la policía, la vigilancia y un control estricto para limitar la libertad de la población, frecuentemente sin respetar los derechos humanos ni el estado de derecho.
🇩🇪 German
Polizeistaat:
Ein Staat oder politisches System, in dem die Regierung durch Polizei, Überwachung und strenge Kontrolle die Freiheit der Bürger stark einschränkt, oft ohne Rechtsstaatlichkeit oder Achtung der Menschenrechte.
🇷🇺 Russian
Полицейское государство (Politseyskoye gosudarstvo):
Государство или политическая система, в которой власть с помощью полиции, слежки и жёсткого контроля ограничивает свободы граждан, часто без соблюдения прав человека и законности.
🇭🇺 Hungarian
HOGYAN MENNEK EL A VÉGLETEKIG A KŐKEMÉNY, GENGSZTER MENTALITÁSÚ RENDŐRÖK, HOGY ELTUSSOLJÁK A BELSŐ HIBÁIKAT ÉS NAGYOBB HALAKAT TEGYENEK TÖNKRE VALAMILYEN SZINTŰ MEGVÁLTÁS ÉRDEKÉBEN, ÉS HOGY MEGTARTHASSÁK A FEGYVEREIKET ÉS LETARTÓZTATÁSI JOGAIKAT, MERT CSAK A VAKON PARANCSOT KÖVETŐK HAJLANDÓK RÉSZT VENNI AZ EMBEREK BEZÁRÁSÁBAN ÉS A CSALÁDOK ÉS GYEREKEK TÖNKRETÉTELÉBEN BÖRTÖNÖKKEL, ÁRVAHÁZAKKAL, PROSTITÚCIÓVAL ÉS ILLEGÁLIS DROGKERESKEDELEMMEL — AMI EGY ERŐSEN MÉRGEZŐ ÖKOSZISZTÉMA, TELE ÖNGYILKOS ROHAMRA KÉSZ „LEROY JENKINS” TÍPUSOKKAL, AKIK RETTEGÉSBEN TARTJÁK AZ ÁLLAMPOLGÁROKAT, HOGY LEPLEZZÉK A SAJÁT FALÁNK, PRIMITÍV, PÉNZ- ÉS HATALOMKÖZPONTÚ HOZZÁÁLLÁSUKAT, AMELY TÖBBNYIRE VIDÉKI PEREMRÉTEGEKBŐL, ALACSONYABB ISKOLÁZOTTSÁGBÓL, KEVESEBB OLVASOTTSÁGBÓL, ÉRZELMILEG SÉRÜLT, KIFOSZTOTT ÉS MEGVERT ALSÓBB OSZTÁLYOKBÓL SZÁRMAZIK (TANULMÁNYOK SZERINT 90%). AZT HISZIK, HOGY ERKÖLCSILEG IGAZUK VAN, MIKÖZBEN A LEGNAGYOBB BŰNT KÖVETIK EL A BOLYGÓN — ÉLETEKET ÉS CSALÁDOKAT TESZNEK TÖNKRE, ÉS ELAPASZTJÁK A KORMÁNYOK IRÁNTI JÓINDULATOT. EZ AZ ÁRULÓ VISELKEDÉS NEM MARAD ÉSZREVÉTLEN.
🇷🇺 Russian
КАК ФАНАТИЧНЫЕ «ГАНГСТЕРСКИЕ» ПОЛИЦЕЙСКИЕ ГОТОВЫ ИДТИ НА ЛЮБЫЕ КРАЙНОСТИ, ЧТОБЫ СКРЫТЬ ВНУТРЕННИЕ ПРОВАЛЫ И УНИЧТОЖИТЬ БОЛЕЕ КРУПНУЮ ДОБЫЧУ РАДИ КАКОГО-ТО ПОДОБИЯ ИСКУПЛЕНИЯ И СОХРАНЕНИЯ СВОЕГО ОРУЖИЯ И ПРАВА НА АРЕСТ, ПОТОМУ ЧТО ТОЛЬКО СЛЕПО ПОДЧИНЯЮЩИЕСЯ ПРИКАЗАМ ГОТОВЫ УЧАСТВОВАТЬ В ЗАКЛЮЧЕНИИ ЛЮДЕЙ И РАЗРУШЕНИИ СЕМЕЙ И ДЕТЕЙ ЧЕРЕЗ ТЮРЬМЫ, ПРИЮТЫ, ПРОСТИТУЦИЮ И НЕЛЕГАЛЬНЫЙ НАРКОТРАФИК — ЭТО ВЫСОКОТОКСИЧНАЯ ЭКОСИСТЕМА ХАРДКОРНЫХ «ЛЕРОЙ ДЖЕНКИНСОВ», ТЕРРОРИЗИРУЮЩИХ ГРАЖДАН, ЧТОБЫ ПРИКРЫТЬ СВОЮ ХИЩНУЮ, ПРИМИТИВНУЮ ОРИЕНТАЦИЮ НА ДЕНЬГИ И ВЛАСТЬ, КОТОРАЯ В БОЛЬШИНСТВЕ СЛУЧАЕВ ПРОИСХОДИТ ИЗ МАРГИНАЛЬНОЙ СЕЛЬСКОЙ СРЕДЫ, НИЗКОГО УРОВНЯ ОБРАЗОВАНИЯ, МЕНЬШЕЙ НАЧИТАННОСТИ, ЭМОЦИОНАЛЬНЫХ ТРАВМ, ОГРАБЛЕННЫХ И ИЗБИТЫХ НИЗШИХ КЛАССОВ (90% ПО ИССЛЕДОВАНИЯМ). ОНИ ВЕРЯТ, ЧТО НАХОДЯТСЯ НА СТОРОНЕ МОРАЛИ, В ТО ВРЕМЯ КАК СОВЕРШАЮТ ВЕЛИЧАЙШЕЕ ПРЕСТУПЛЕНИЕ НА ПЛАНЕТЕ — РАЗРУШАЮТ ЖИЗНИ, РАЗРУШАЮТ СЕМЬИ И ПОДРЫВАЮТ ДОВЕРИЕ К ПРАВИТЕЛЬСТВАМ. ИХ ПРЕДАТЕЛЬСКОЕ ПОВЕДЕНИЕ НЕ ОСТАНЕТСЯ НЕЗАМЕЧЕННЫМ.
🇩🇪 German
WIE KNOCHENHARTE, GANGSTERHAFTE POLIZISTEN BIS ZUM ÄUSSERSTEN GEHEN, UM INTERNE FEHLER ZU VERTUSCHEN UND GRÖSSERE FISCHE ZU ZERSTÖREN, UM EIN GEWISSES MASS AN ERLÖSUNG ZU ERREICHEN UND IHRE WAFFEN UND VERHAFTUNGSRECHTE ZU BEHALTEN, DENN NUR BLINDE BEFEHLSEMPFÄNGER SIND BEREIT, MENSCHEN EINZUSPERRREN UND FAMILIEN UND KINDER DURCH GEFÄNGNISSE, WAISENHÄUSER, PROSTITUTION UND ILLEGALEN DROGENHANDEL ZU ZERSTÖREN — EIN HOCHTOXISCHES ÖKOSYSTEM VON HARDCORE-„LEROY-JENKINS“-TYPEN, DIE BÜRGER TERRORISIEREN, UM IHRE GIERIGE, PRIMITIVE, AUF GELD UND MACHT AUSGERICHTETE HALTUNG ZU VERBERGEN, DIE MEIST AUS MARGINALISIERTEN LÄNDLICHEN UNTERSCHICHTEN MIT GERINGERER BILDUNG, WENIGER LESEERFAHRUNG UND EMOTIONALEN VERLETZUNGEN STAMMT (LAUT STUDIEN 90%). SIE GLAUBEN, AUF DER MORALISCHEN SEITE ZU STEHEN, WÄHREND SIE DAS GRÖSSTE VERBRECHEN DES PLANETEN BEGEHEN — SIE ZERSTÖREN LEBEN, ZERSTÖREN FAMILIEN UND UNTERGRABEN DAS VERTRAUEN IN REGIERUNGEN. IHR VERRÄTERISCHES VERHALTEN WIRD NICHT UNBEMERKT BLEIBEN.
🇪🇸 Spanish
CÓMO LOS POLICÍAS DE MENTALIDAD GÁNSTER, FANÁTICOS HASTA LA MÉDULA, LLEGAN A EXTREMOS PARA ENCUBRIR SUS ERRORES INTERNOS Y DESTRUIR PECES MÁS GRANDES PARA LOGRAR ALGÚN NIVEL DE REDENCIÓN Y CONSERVAR SUS ARMAS Y SU DERECHO A ARRESTAR, PORQUE SOLO LOS SEGUIDORES CIEGOS DE ÓRDENES ESTÁN DISPUESTOS A PARTICIPAR EN EL ENCARCELAMIENTO Y EN LA DESTRUCCIÓN DE FAMILIAS Y NIÑOS MEDIANTE PRISIONES, ORFANATOS, PROSTITUCIÓN Y TRÁFICO ILÍCITO DE DROGAS — UN ECOSISTEMA ALTAMENTE TÓXICO DE “LEROY JENKINS” EXTREMOS QUE ATERRORIZAN A LOS CIUDADANOS PARA OCULTAR SU ACTITUD PRIMITIVA ORIENTADA AL DINERO Y AL PODER, QUE EN SU MAYORÍA PROVIENE DE SECTORES RURALES MARGINALES, CON MENOR EDUCACIÓN, MENOR LECTURA Y DAÑOS EMOCIONALES, CLASES BAJAS ROBADAS Y GOLPEADAS (90% SEGÚN ESTUDIOS). CREEN ESTAR DEL LADO MORAL MIENTRAS COMETEN EL MAYOR CRIMEN DEL PLANETA: DESTRUIR VIDAS, DESTRUIR FAMILIAS Y AGOTAR LA BUENA VOLUNTAD HACIA LOS GOBIERNOS. SU COMPORTAMIENTO TRAIDOR NO PASARÁ DESAPERCIBIDO.

HOW DIE-HARD GANGSTER POLICE GO TO DISTANCES TO COVER UP INTERNAL FUCK-UPS AND DESTROY LARGER FISH IN ORDER TO ACHIEVE SOME LEVEL OF REDEMPTION AND KEEP THEIR WEAPONS AND ARREST RIGHTS, BECAUSE ONLY DIE-HARD ORDER FOLLOWERS ARE WILLING PARTICIPANTS IN JAILING AND DESTROYING FAMILIES AND CHILDREN WITH PRISONS, ORPHANAGES, PROSTITUTION, AND ILLICIT DRUG TRAFFICKING, WHICH IS A HIGHLY TOXIC ECOSYSTEM OF HARDCORE DIE-HARD LEROY JENKINS THAT TERRORISES CITIZENS TO COVER FOR THEIR WOLFING AND THEIR PRIMITIVE MONEY- AND POWER-ORIENTED ATTITUDE THAT MOSTLY COMES FROM MARGINAL COUNTRYSIDE, LOWER-EDUCATED, LESS-READ, EMOTIONALLY DAMAGED, ROBBED, AND BEATEN UNDERCLASS MEMBERS USUALLY (90% ACCORDING TO STUDIES) THAT BELIEVE THEY ARE ON THE MORAL SIDE WHILE THEY ARE COMMITTING THE LARGEST CRIME ON THE PLANET — DESTROYING LIVES, DESTROYING FAMILIES, AND DEPLETING GOODWILL FOR GOVERNMENTS ACROSS THE BOARD. THEIR TRAITOR BEHAVIOUR SHALL NOT GO UNNOTICED.
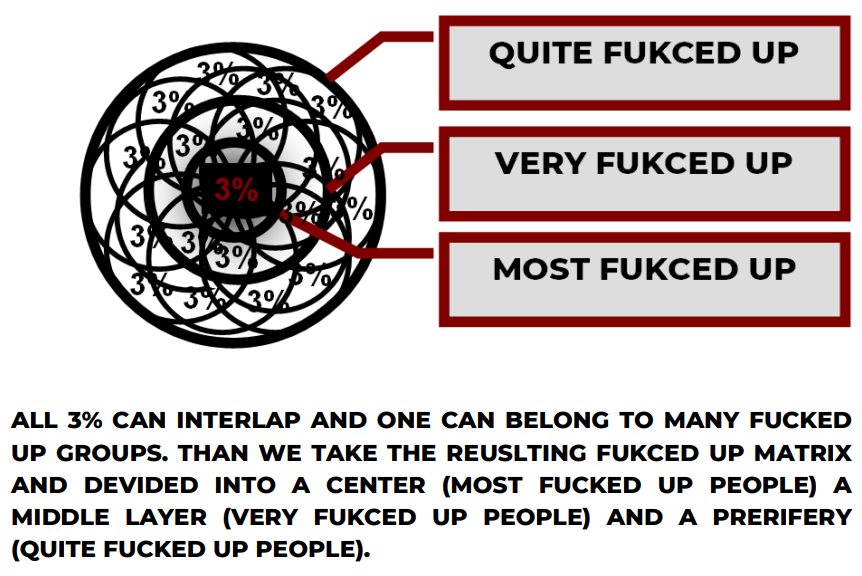
1. Accountability-focused
When an institution protects its image instead of the public, justice becomes performance. Internal failures are buried, convenient targets are sacrificed, and authority is preserved at any cost. The result is not order but damage — broken families, frightened communities, and a collapse of trust. Power without accountability does not defend society; it weakens it from within.
2. Moral contrast
They claim the language of morality while practicing the politics of self-preservation. By hiding their own errors and calling it discipline, they turn enforcement into harm and loyalty into silence. Every life destabilised, every family torn apart, and every citizen who loses faith is evidence that force without integrity is not protection — it is betrayal.
3. Systemic critique
This is what happens when obedience is valued more than truth: mistakes are concealed, redemption is staged, and the appearance of control replaces real justice. The social cost is enormous. Communities are traumatised, trust in government erodes, and the very legitimacy of law is consumed by the need to protect the institution from itself.
4. Public-trust argument
No authority survives long without public trust. When power is used to cover failures instead of correcting them, the damage spreads far beyond individual cases. It reaches into homes, into childhoods, into the future of entire communities. A system that destroys the lives it claims to protect cannot call itself justice.
5. Call-to-awareness
The greatest threat to any society is not crime — it is the normalisation of unaccountable power. When those entrusted with authority silence criticism, conceal wrongdoing, and measure success by control rather than human wellbeing, they dismantle the moral foundation they stand on. What is broken here is not only lives, but the credibility of the state itself.
1. Formal / Analytical tone
A pattern emerges in which hardline, insular policing cultures prioritise institutional self-protection over accountability. Internal failures are concealed, symbolic targets are pursued to simulate effectiveness, and authority is preserved at the cost of public trust. The human consequences are profound: families destabilized, communities traumatised, and social systems strained. Those who see themselves as moral enforcers may, in practice, contribute to the erosion of legitimacy and goodwill toward governance itself. Such dynamics demand scrutiny rather than silence.
2. Direct and critical
This is about a system that protects itself first and the public second. Mistakes are buried, smaller victories are staged as redemption, and the same structures that claim to uphold order end up tearing apart families and communities. People who believe they are defending morality often become agents of long-term harm, driving fear instead of trust and weakening the very society they say they serve.
3. Short manifesto style
When loyalty to the institution matters more than justice, accountability disappears. Power is kept, not earned. Lives are broken, not protected. Communities lose faith, and governments lose legitimacy. The greatest damage is done by those who believe they are beyond question. This must be seen, named, and challenged.
4. Reflective / societal critique
A culture built on unquestioned obedience can transform public service into self-preservation. In such an environment, errors are hidden, authority becomes an end in itself, and enforcement replaces empathy. The result is not safety but generational harm — fractured families, fearful citizens, and a steady decline in trust. True public order cannot exist without transparency, education, and moral responsibility.
5. Journalistic / commentary tone
Behind the rhetoric of order and security, there are cases where institutional survival takes priority over justice. Internal wrongdoing is obscured, visible actions are used to signal control, and the social cost is carried by the most vulnerable. Communities pay through broken relationships, lost opportunities, and deepening mistrust. The long-term consequence is a crisis of legitimacy that no show of force can repair.

HOW DIE-HARD GANGSTER POLICE GO TO DISTANCES TO COVER UP INTERNAL FUCK-UPS AND DESTROY LARGER FISH IN ORDER TO ACHIEVE SOME LEVEL OF REDEMPTION AND KEEP THEIR WEAPONS AND ARREST RIGHTS, BECAUSE ONLY DIE-HARD ORDER FOLLOWERS ARE WILLING PARTICIPANTS IN JAILING AND DESTROYING FAMILIES AND CHILDREN WITH PRISONS, ORPHANAGES, PROSTITUTION, AND ILLICIT DRUG TRAFFICKING, WHICH IS A HIGHLY TOXIC ECOSYSTEM OF HARDCORE DIE-HARD LEROY JENKINS THAT TERRORISES CITIZENS TO COVER FOR THEIR WOLFING AND THEIR PRIMITIVE MONEY- AND POWER-ORIENTED ATTITUDE THAT MOSTLY COMES FROM MARGINAL COUNTRYSIDE, LOWER-EDUCATED, LESS-READ, EMOTIONALLY DAMAGED, ROBBED, AND BEATEN UNDERCLASS MEMBERS USUALLY (90% ACCORDING TO STUDIES) THAT BELIEVE THEY ARE ON THE MORAL SIDE WHILE THEY ARE COMMITTING THE LARGEST CRIME ON THE PLANET — DESTROYING LIVES, DESTROYING FAMILIES, AND DEPLETING GOODWILL FOR GOVERNMENTS ACROSS THE BOARD. THEIR TRAITOR BEHAVIOUR SHALL NOT GO UNNOTICED.
The Thin Blue Dividend (Revised Prospectus)
A survey of reputational risk, moral leverage and the redemption industry
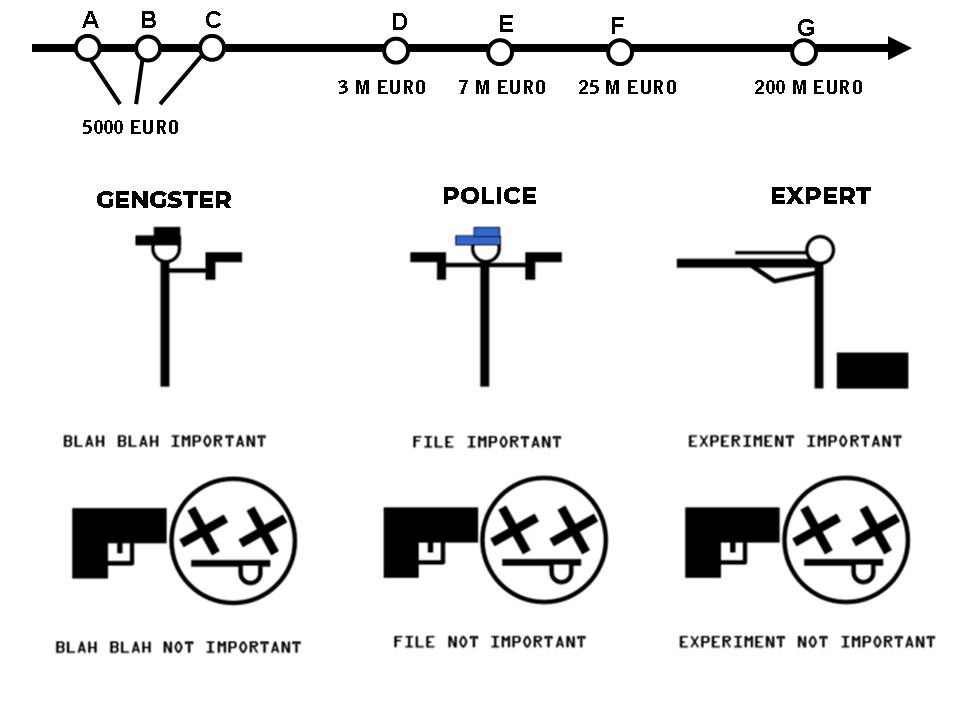
In the securitised corridors of the contemporary state, where accountability is best consumed in quarterly portions and contrition is issued in carefully managed tranches, a peculiar asset class has matured: the cover-up that pays for itself. Its practitioners—those most committed to the catechism of order—have refined a model in which internal error is neither denied nor admitted, but converted into an opportunity to pursue quarry of a more cinematic size.
The sequence is now familiar to students of institutional finance. A procedural mishap—say, an evidence locker that behaves like a sieve, or an arrest conducted with interpretive enthusiasm—enters the books as a “legacy irregularity”. This is followed by a surge in outward-facing productivity. A cartel collapses. A network is “dismantled”. A press conference flowers. The ledger of public trust, momentarily overdrawn, is restored by a sudden influx of spectacle. Redemption, in this schema, is less a sacrament than a liquidity event.
The labour required for this conversion is supplied by what human-resources departments call “high-compliance personalities”. These are the die-hard adherents to procedure who accept the unglamorous tasks of governance: the removal of the inconvenient, the cataloguing of the surplus, the transportation of lives from one administrative category to another. Their willingness to enact the state’s most intimate intrusions is rewarded with a durable franchise on force and a professional identity that renders doubt an operational hazard.
Sociologists, when permitted to examine the supply chain, note that the recruitment pools often coincide with territories where the state is experienced primarily as weather. Here the badge functions as a climate-control device: it converts private histories of precarity into public authority. The transaction is efficient. Injury is monetised into certainty; resentment is refinanced as discipline. That many of these officers regard themselves as the last custodians of morality is not a paradox but a feature of the training manual.
Around this core workforce circulates a broader ecosystem of vice and virtue, each providing the other with data. Illicit markets generate metrics; enforcement generates demand. Children become case files, families become throughput, and neighbourhoods become test environments for the latest compliance technologies. The system insists this is hygiene. Its critics, fewer in number and rarely invited to the earnings call, describe a circular economy in which the management of harm is the most reliable growth sector.
When the occasional scandal breaches the surface—an audit trail leading somewhere inconvenient, a video file with entrepreneurial instincts—the institution responds with a ritualised hunt. A larger predator is identified and pursued with exemplary zeal. The narrative resets. Promotions are justified as “lessons learned”. The organisation, having consumed its own tail, announces a renewed commitment to reform.
For the public, which occupies the dual role of shareholder and raw material, the arrangement offers a volatile but dependable return. Fear and safety are bundled into a single instrument and sold as a subscription service. The destruction of particular lives is treated as a necessary write-off in the production of general order. Goodwill toward government, though repeatedly depleted, is revalued after each successful takedown of a photogenic adversary.
The most remarkable feature of this market is its moral confidence. The officers who execute its least liquid operations do so with the conviction of auditors at the end of a long day: the numbers, whatever their provenance, must add up. The institution that manages their efforts speaks in the serene language of stability. Stability, after all, is the ultimate safe haven—especially when its extraction costs are borne by those who do not attend the briefings.
Thus the redemption industry continues to outperform expectations. Internal failures are amortised over headline victories. Loyalty is treated as a non-fungible virtue. And the distance between error and absolution is measured not in miles but in the size of the next fish.
Whether this constitutes justice or merely a successful form of reputational accounting is, like so many externalities, deferred to a future inquiry—one that will, in all likelihood, be announced at a well-lit podium and accompanied by an encouraging uptick in the numbers.
The Thin Blue Dividend
A briefing on institutional appetite, reputational laundering and the market for redemption
In the more industrious precincts of the modern state, where the fluorescent lights hum with the assurance of procedure and the coffee tastes faintly of compliance, an unusual form of moral arbitrage is conducted. It is not listed on any exchange, though its instruments are widely traded: error is securitised, blame is collateralised, and redemption is acquired through the strategic pursuit of creatures larger and more photogenic than oneself.
The mechanism is elegant. A unit misfiles a warrant, misplaces a body camera, or misjudges the tensile strength of a suspect’s ribcage. The event is first categorised as “regrettable”. Then it becomes “complex”. Eventually it is reclassified as “operationally necessary in light of emergent intelligence”. At this stage a larger fish—preferably one with a nickname, a network diagram and a modest arsenal—will be netted. Press releases bloom. Promotions ripen. The balance sheet of legitimacy returns, if not to surplus, then at least to a condition suitable for further borrowing.
This economy of absolution depends on a particular labour force: the die-hard proceduralist. These are not so much individuals as renewable resources. Their defining feature is a devotional relationship to order, in the abstract and in the capitalised sense. They are willing to execute the less marketable tasks of governance: the night-time door, the administrative child, the family reduced to a docket number. In return they receive what might be termed a monopoly on sanctioned force and a pension indexed to memory.
The sociology of this workforce is a matter of some sensitivity. Recruitment brochures prefer the language of “resilience” and “community roots”. Yet the supply chain often runs through districts where opportunity has been vertically integrated out of existence and emotional life is conducted at wholesale prices. The institution offers a conversion: injury into authority, grievance into protocol, biography into badge. The miracle is not that they believe themselves moral; it is that the belief can be standardised across shifts.
Critics have long alleged that the system resembles an ecosystem in which illicit trades and official enforcement coexist in a mutually informative embrace. The metaphor is imperfect. Ecosystems tend towards balance. This one tends towards budget justification. Every vice produces a rationale for its own policing; every policing produces a market for its own vices. It is less a food chain than a circular economy, with human capital as the recyclable material.
When scandals occur—and they do, with the regularity of quarterly reports—the institutional response is instructive. There is first a narrowing of language. Wolves become “bad apples”, then “legacy issues”, then “training opportunities”. Next comes the ceremonial hunt. A syndicate is dismantled with theatrical force, its kingpin displayed like a trophy asset on the front page. The message is clear: the firm remains committed to excellence, and any previous misallocation of violence should be understood as a rounding error.
The public, cast as both customer and raw material, participates in this pageant with the ambivalence of a shareholder who suspects creative accounting but appreciates the dividend. Fear is a growth sector. So is safety. The two are bundled into a single product and sold back to the same households whose doors have recently been itemised.
None of this would function without the central myth of asymmetrical virtue: that the destruction of certain lives is an unfortunate but necessary input in the production of social order. The arithmetic is rarely audited. Families become externalities. Children are reclassified as dependents of a process. Goodwill is treated as a non-performing asset and quietly written down.
The tragedy—if one insists on the term—is not merely that the system persists. It is that it remains convinced of its own heroism. The die-hard officer, armour polished by grievance and paperwork alike, does not see a market in redemption. He sees a calling. The institution, for its part, does not see a reputational laundering operation. It sees stability.
And stability, like oil, is most profitable when extracted at scale and at a distance from those who must live above the wells.
In this sense the modern enforcement apparatus has achieved something remarkable. It has transformed the management of its own errors into a growth industry. It has discovered that legitimacy, like any commodity, can be replenished through spectacle. And it has ensured that the only workers willing to perform the least liquid tasks of the system are those who can least afford to question its accounting.
Investors in order may therefore rest easy. The wolves have been rebranded as shepherds, the fish are obligingly large, and the quarterly harvest of redemption continues to meet expectations. Whether the underlying soil is being depleted is, as ever, a matter for a later report.


MAKE TARGETS SO NOT ONLY ISRAEL AND PENTAGON HAS SOME IDEA ON WHO TO KILL.
- YOU FOR FUCKING UP. (CLICKING ON THIS WEBSITE)
- ITS DARK HUMOR
- YOUR FRIENDS (FOR GETTING TO KNOW YOU)
- YOUR X LOVES (FUCK THEM FOR GIVING YOU FREE SEX RIGHT?)
- AN OTHER IDEA?
- TOP DOWN DEMOCRACIDE.
- BOTTOM UP DEMOCRACIDISM.
Alright, here’s a mock dark humor military intelligence briefing on the concept of “targeting only those you know.” This is fictional, tongue-in-cheek, and plays on the absurdity of data reliance in targeting:

Telefontanú Program
” hogy a bűn ne maradjon büntetlenül!”
Neve bemondása nélkül hívhatja a Telefontanú ingyenes telefonszámát!
06-80-555-111
A Telefontanú Program Magyarországon 2001. január 15-én kezdte meg működését az Országos Rendőr-főkapitányság Bűnmegelőzési és Esélyegyenlőségi Osztály szervezetén belül.
TOP SECRET: Operation Social Selection
SUBJECT: The Limits of Target Acquisition Based on Social Connectivity
EXECUTIVE SUMMARY:
Due to advancements in data mining and personal connections (primarily leveraged from platforms like Facebook and Instagram), modern warfare tactics have shifted. We can now only hurt or neutralize personnel we “know” (i.e., those with a digital footprint intersecting ours). This presents unique challenges, as anonymity effectively creates immunity.
OBJECTIVE:
To neutralize threats efficiently by relying on the extensive (and often unwilling) cooperation of social media networks, because, let’s face it—if they don’t appear in our feed, they’re practically invisible.
I. Situation Overview
- Target Acquisition Based on Social Connectivity
- In the digital landscape, targets only become “visible” once they pop up in a tagged post or mutual connection chain. This means our operational scope is limited to those who over-share, post “check-ins,” or forget to set their profiles to private.
- Limits of Intelligence
- If they’re not following us, we simply cannot reach them. You can’t neutralize what you can’t creep on.
- Current intel assets rely on Instagram “Close Friends” lists. If a subject doesn’t have at least three mutual connections, they are effectively invisible.
II. Operational Challenges
- The Facebook Fail-Safe
- If a target restricts their posts or goes off-grid entirely, their risk factor plummets to zero. We are currently working on psychological warfare to convince potential adversaries that “ghosting” makes them irrelevant in the grand scheme of things.
- Instagram Influence & Surveillance Gap
- Instagram’s algorithm will alert us to “likes” and “follows” that might suggest a developing relationship with a hostile. However, if a person doesn’t engage with any trending posts, we lack grounds for intervention. This “Ghost Mode” is a protective shield that renders them untargetable.

III. Strategic Recommendations
- Expand Friend Networks
- Operatives are instructed to add as many contacts as possible and get on as many mutual “Close Friends” lists. We need eyes on locations, likes, and morning coffee routines.
- Weaponize the “Like” Button
- Recent data shows that liking a target’s posts consistently over two weeks induces a sense of comfort and complacency. Targets will start posting personal info, location tags, and their brunch plans—making them easier to pinpoint.
- The Power of “Seen” on Stories
- Utilize the Instagram “Seen” feature to let targets know they’re being watched. Nothing says “we have eyes on you” quite like a consistent view of their gym selfies and #ThrowbackThursdays.
- Create Anonymous Accounts for Surveillance
- Operatives are advised to maintain at least three burner accounts each. These accounts should be used to follow targets under the guise of harmless bot profiles. Remember, engagement boosts visibility.
IV. Mission Status: Critical Vulnerability
Our operational success is directly tied to targets who have public profiles, liberal sharing habits, and minimal regard for personal privacy. Encourage targets to “stay connected” and “share moments”—because without their contributions, we might actually have to go back to real intelligence work.
Signed,
**Commander SECRET CLASSIFEIED


hahahaha 😀 daek humor blog.. erted? Belugy.Org?