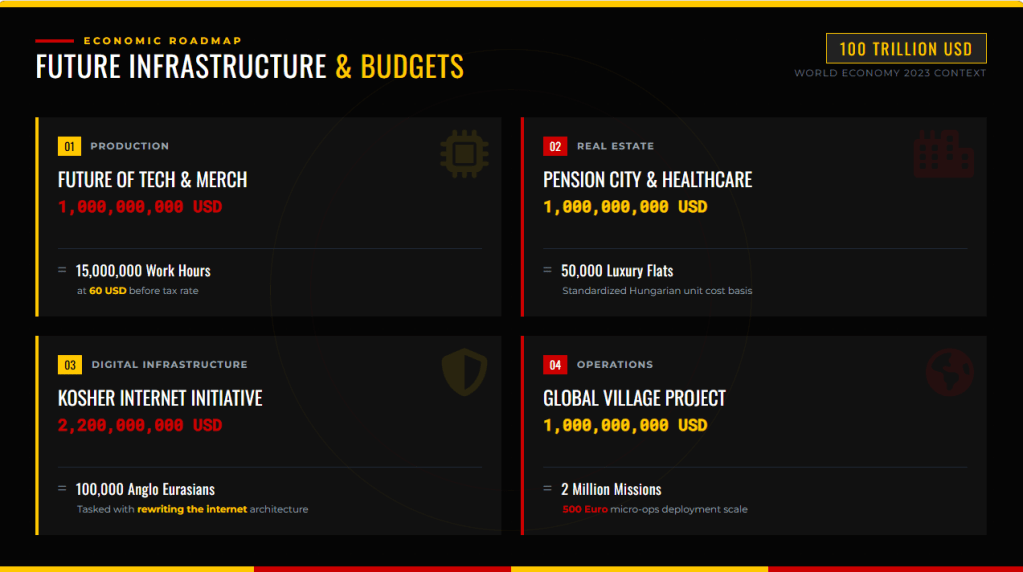
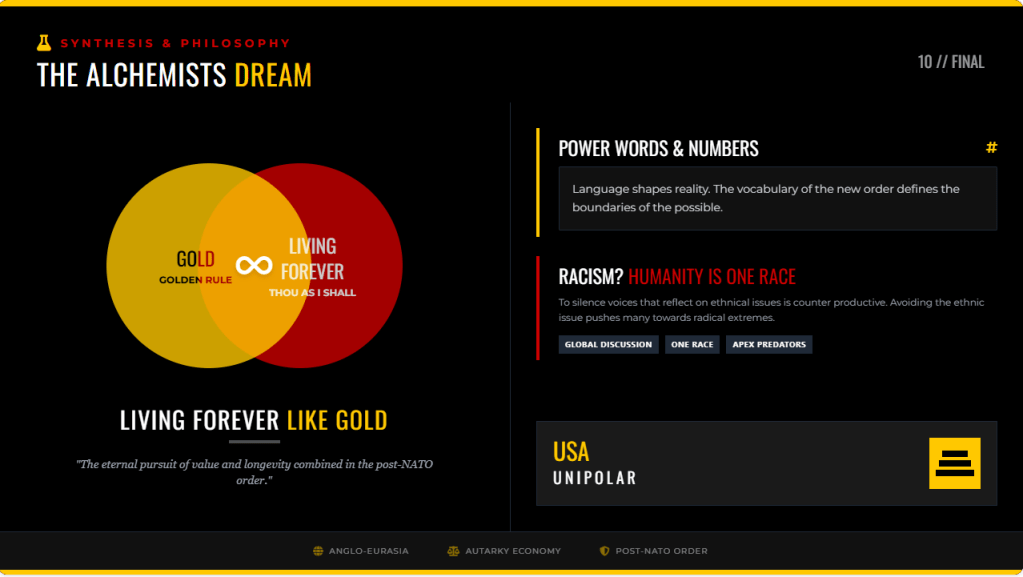
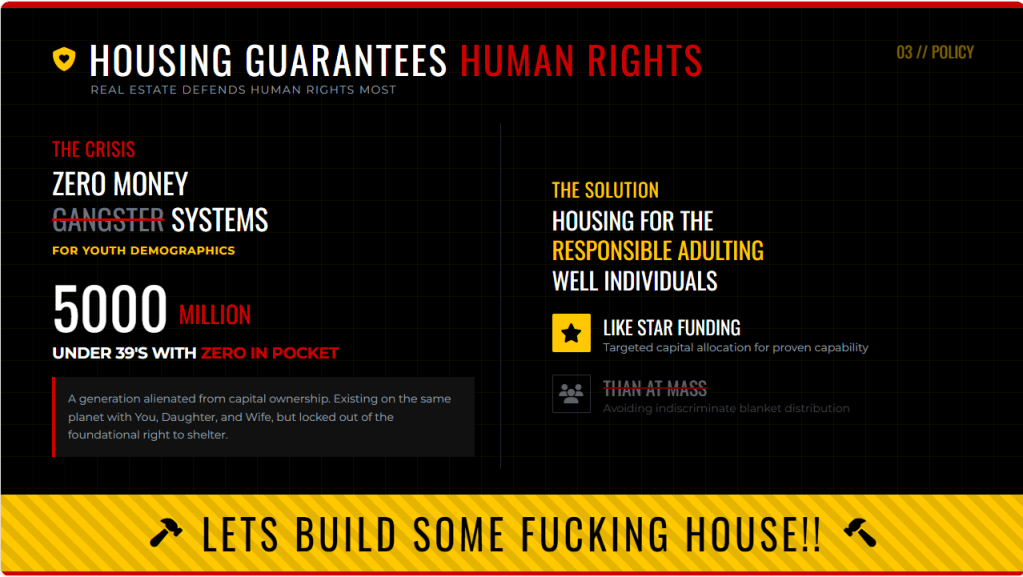
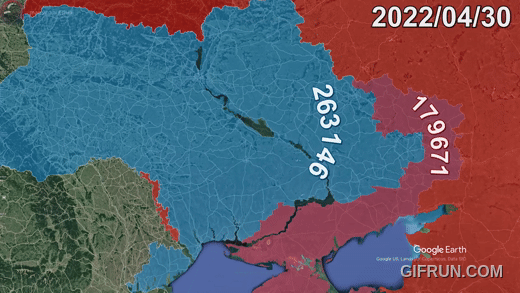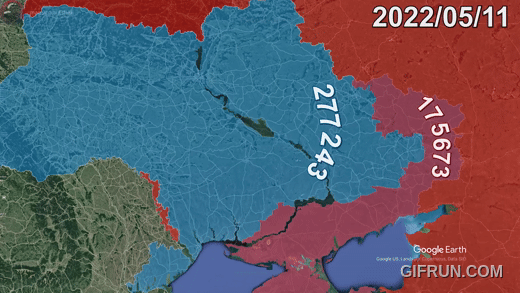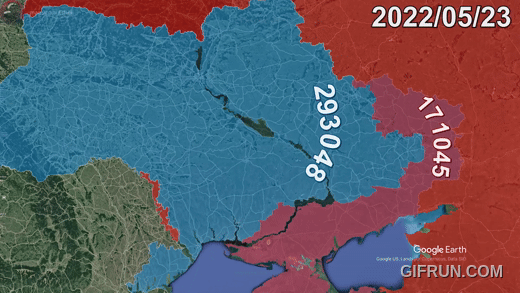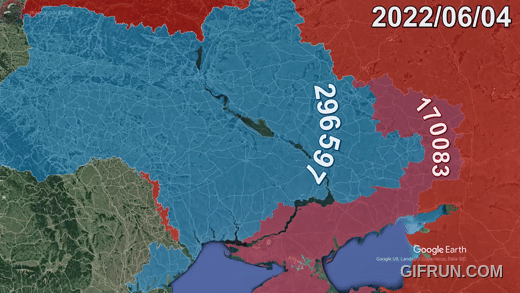
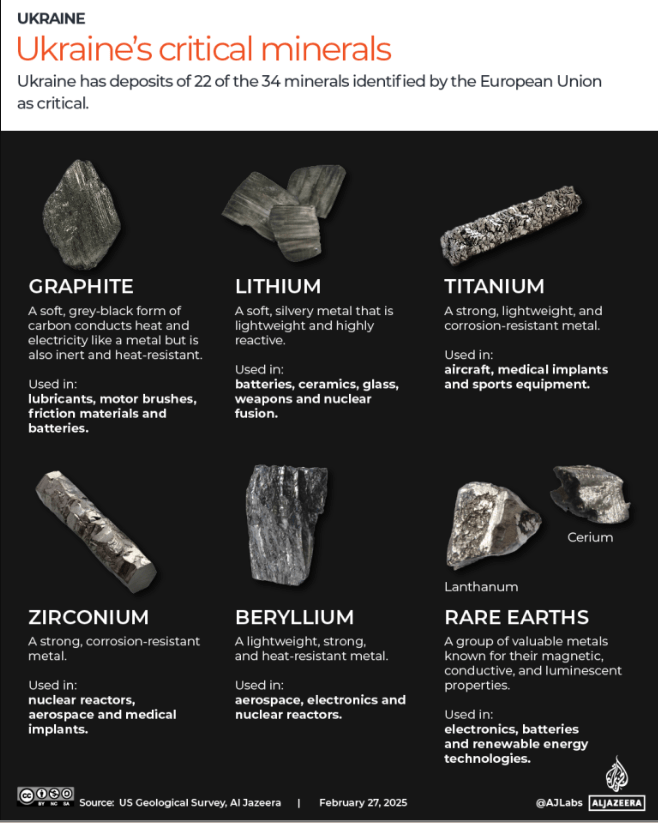
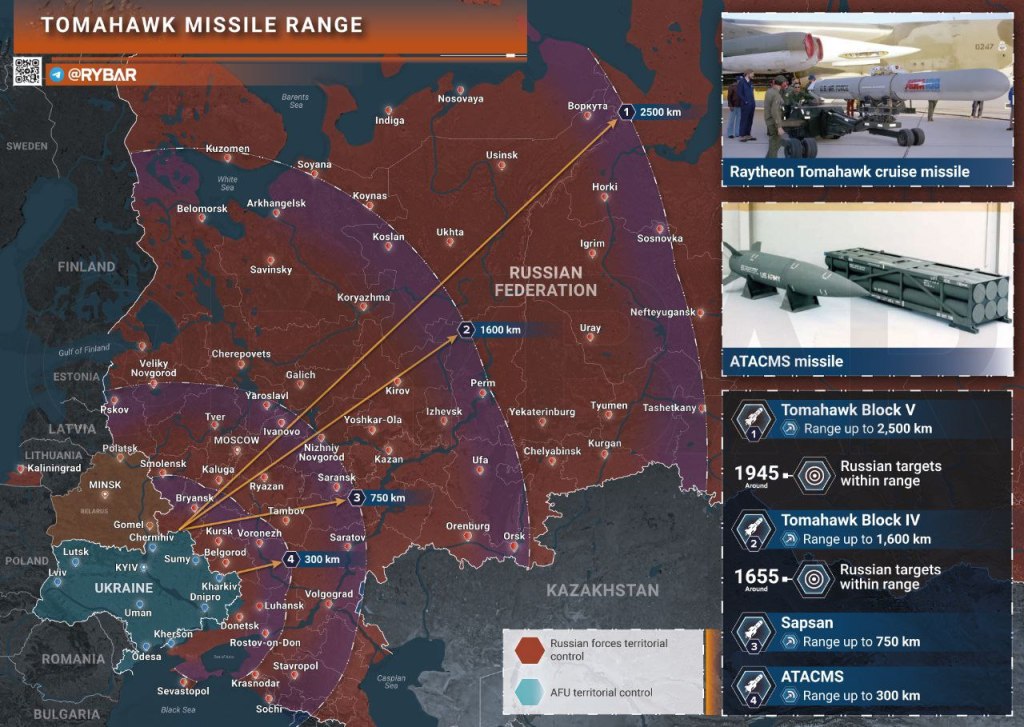
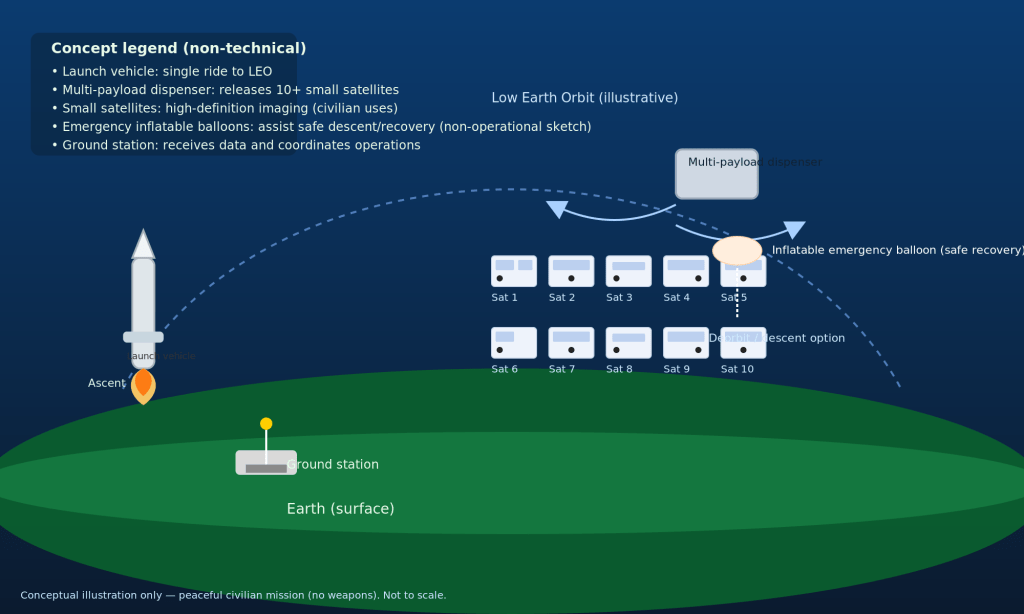
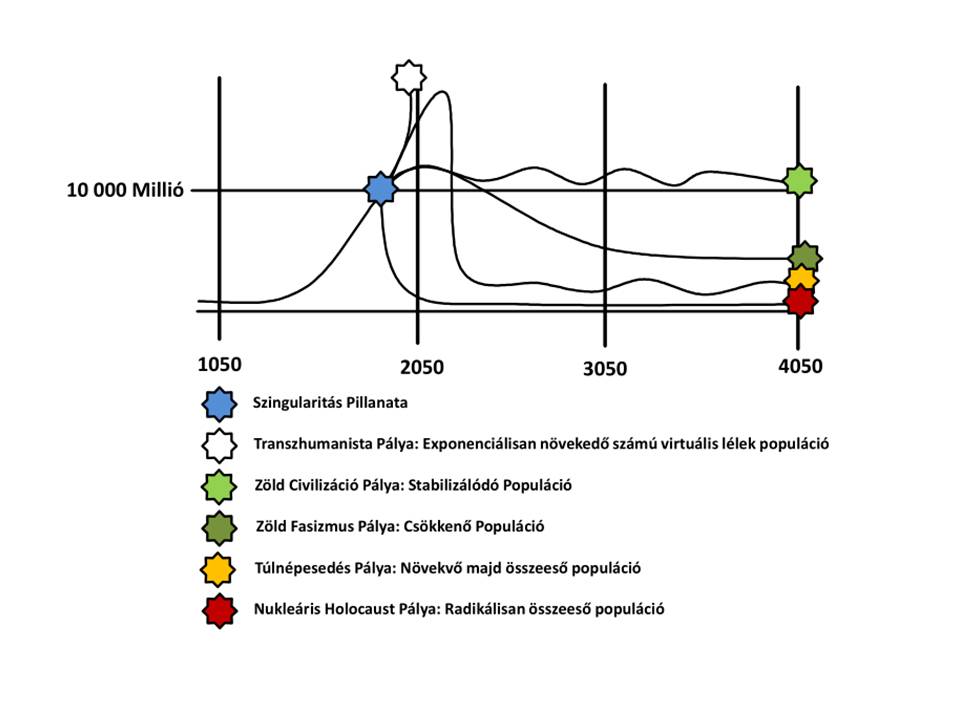
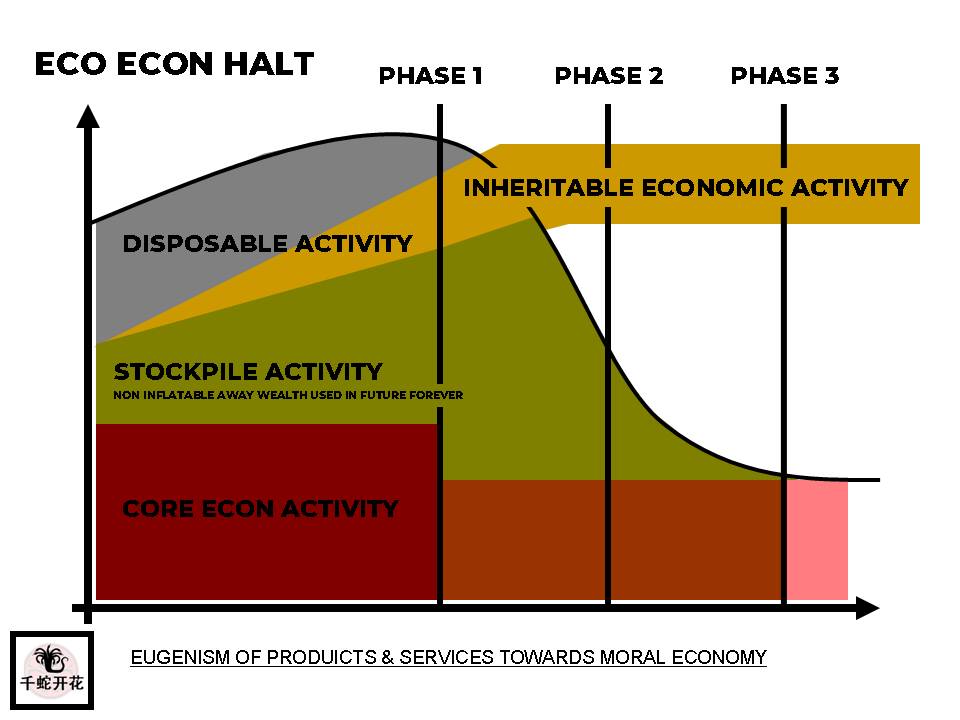
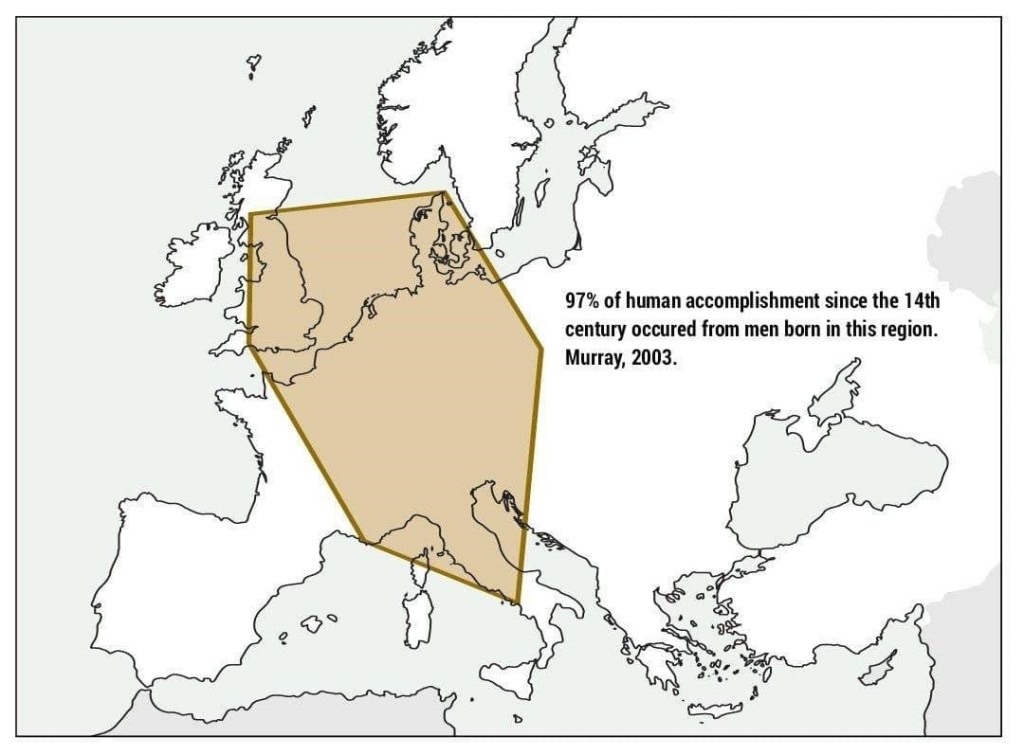
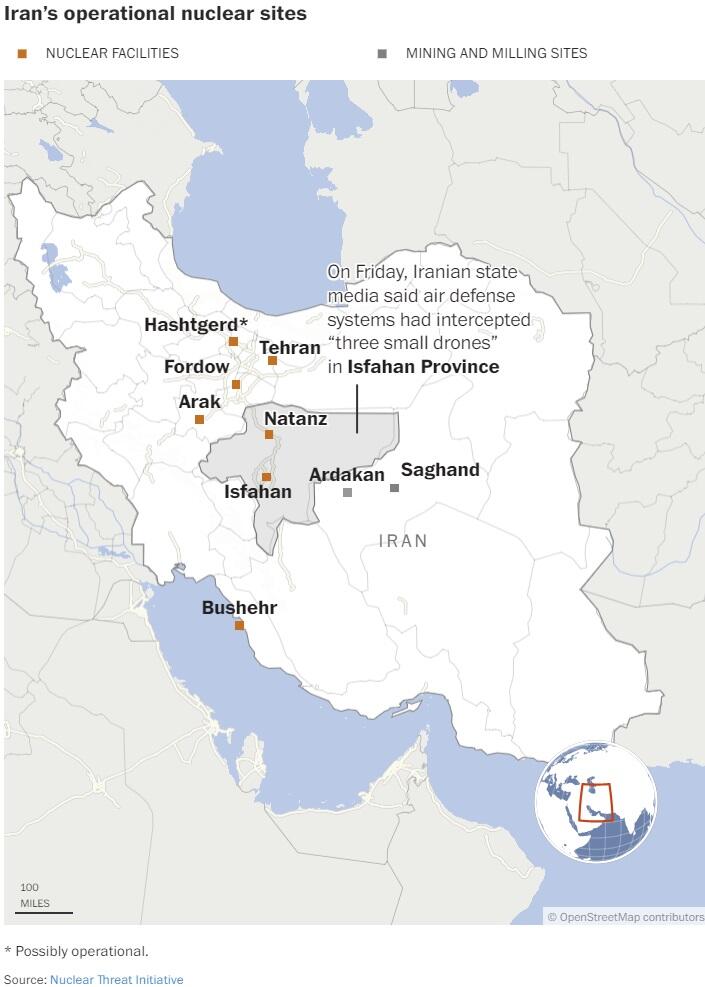
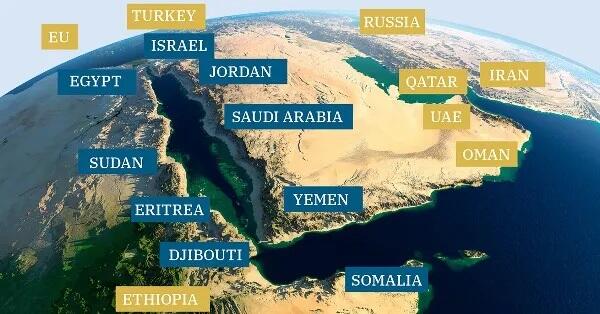
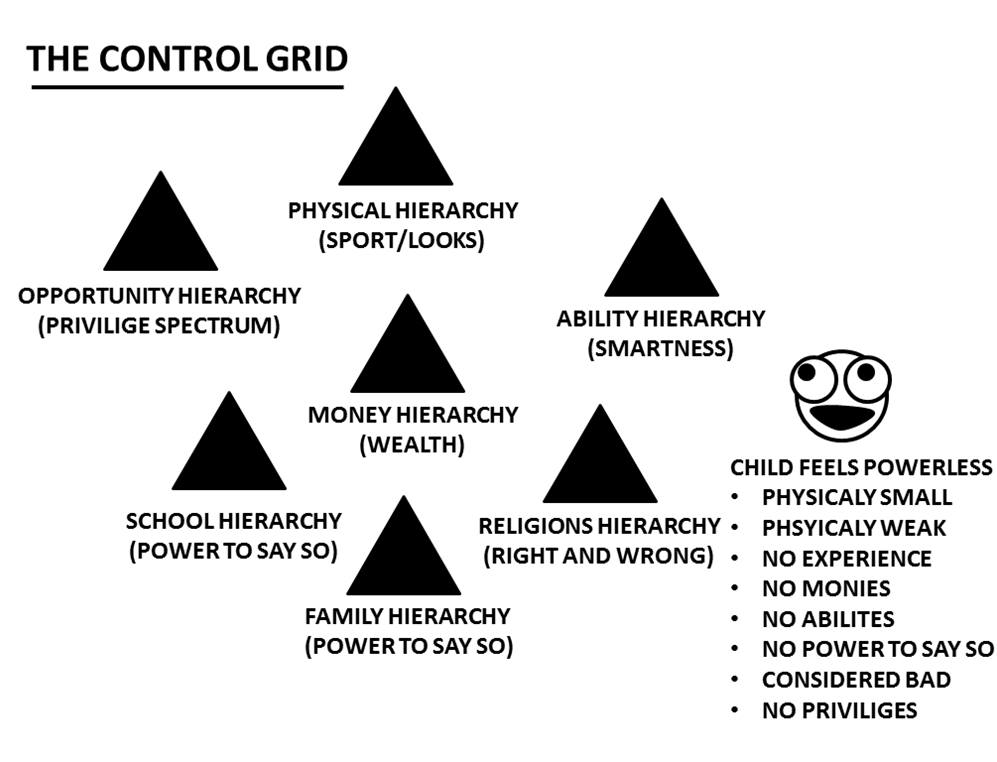
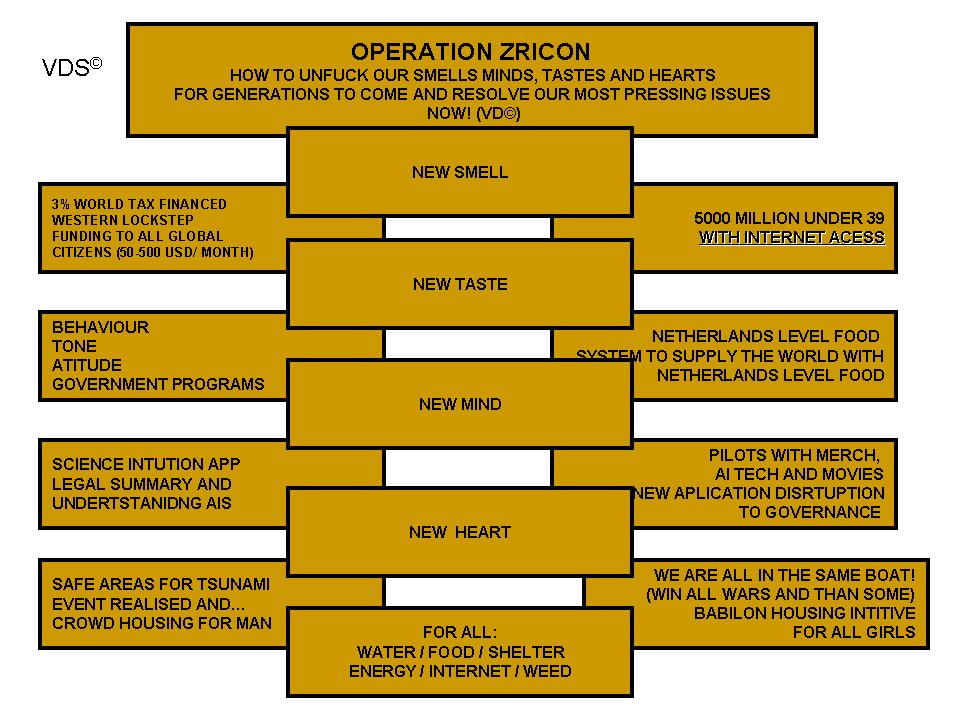
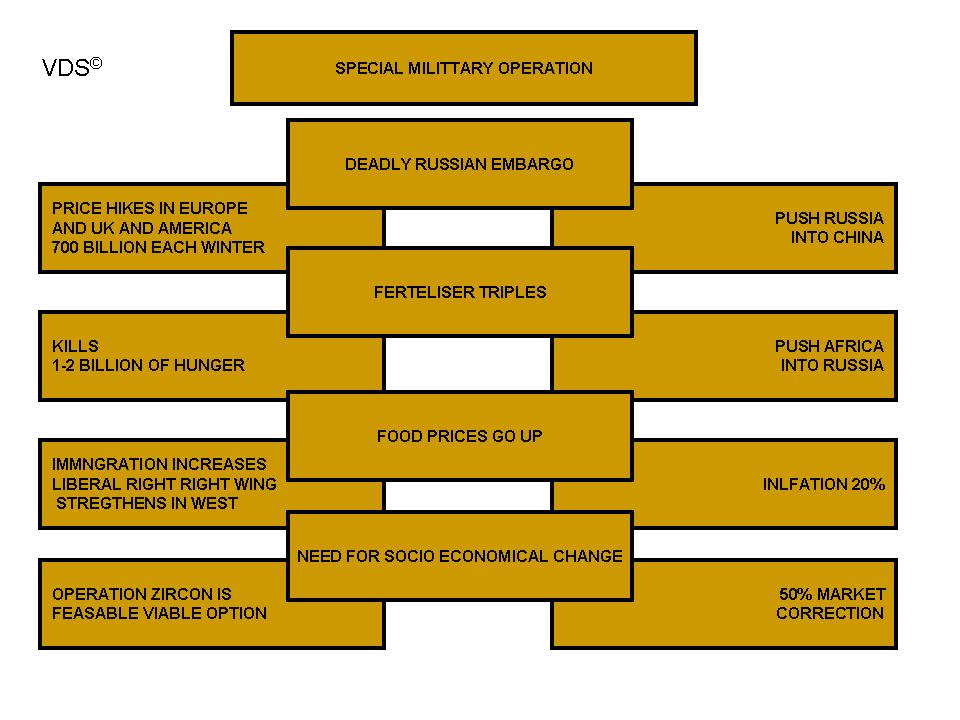
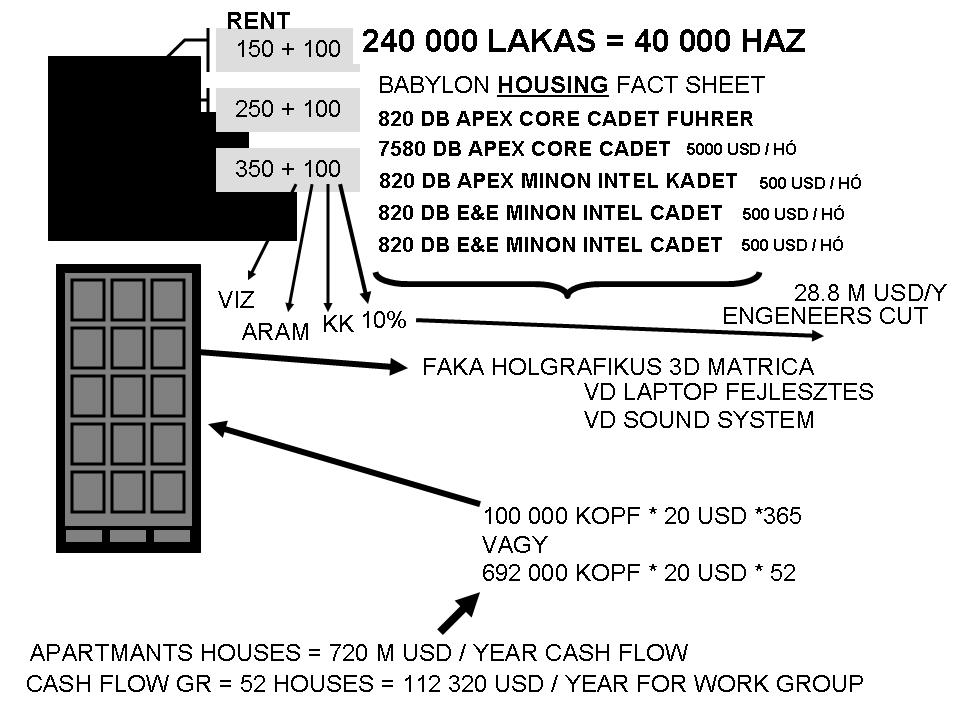
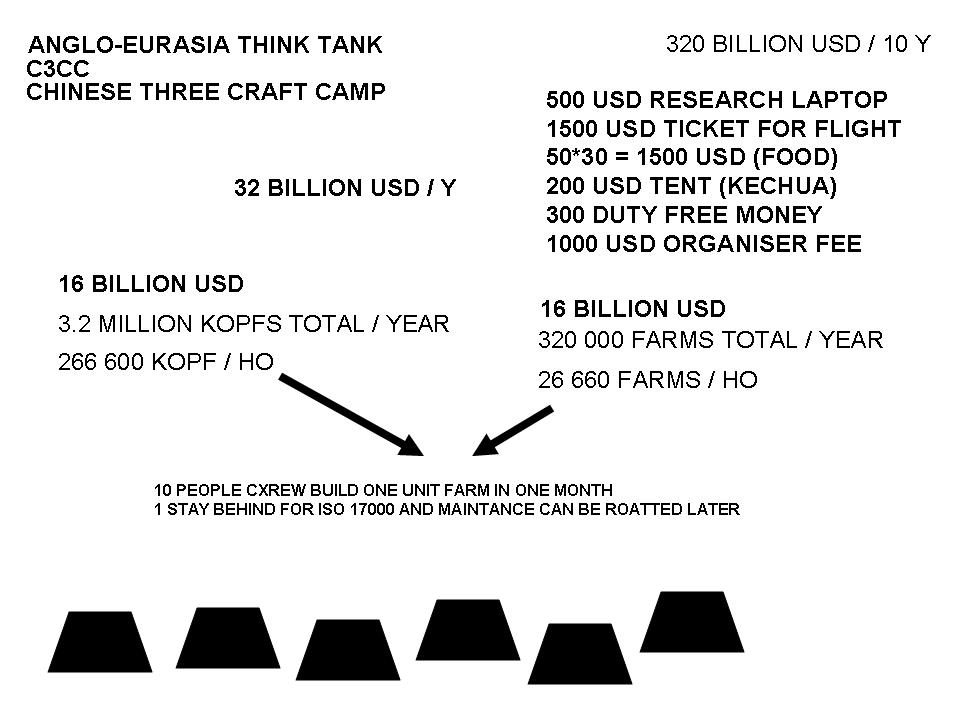
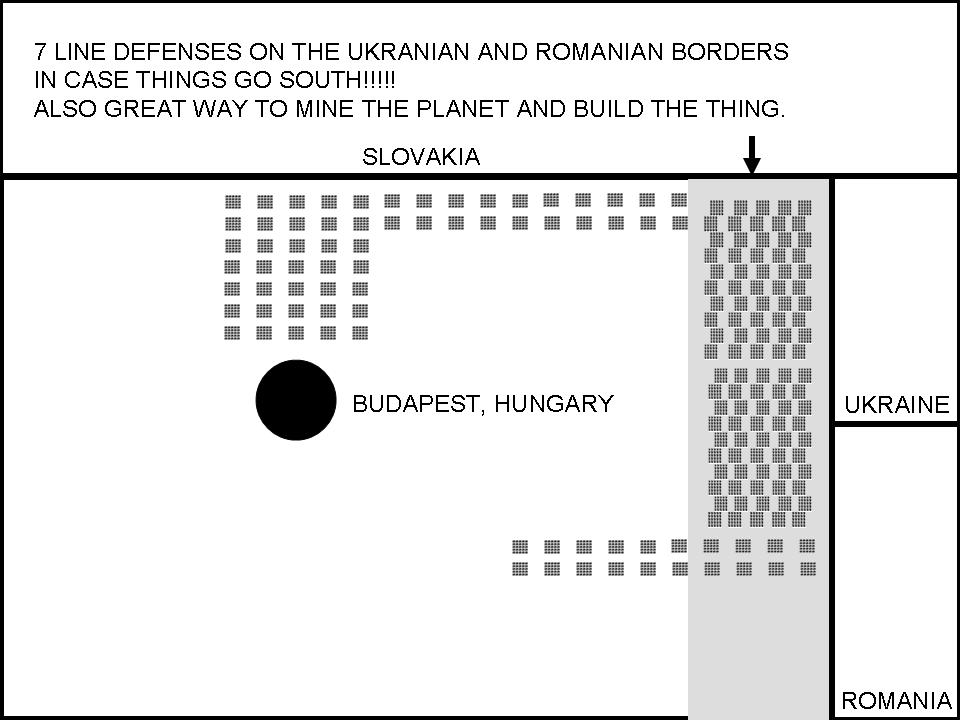
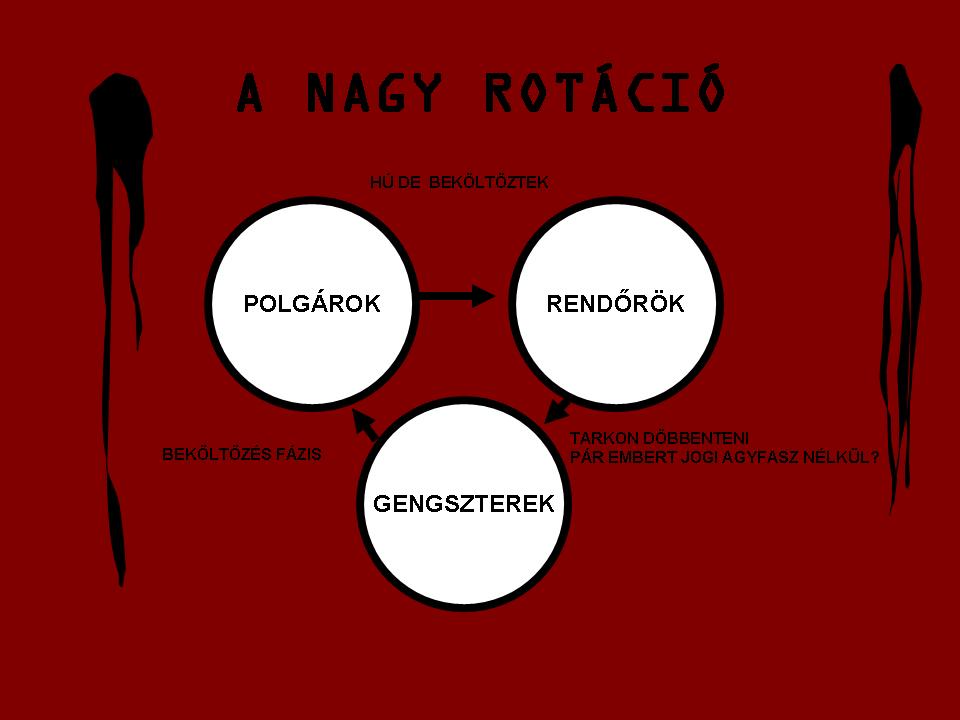
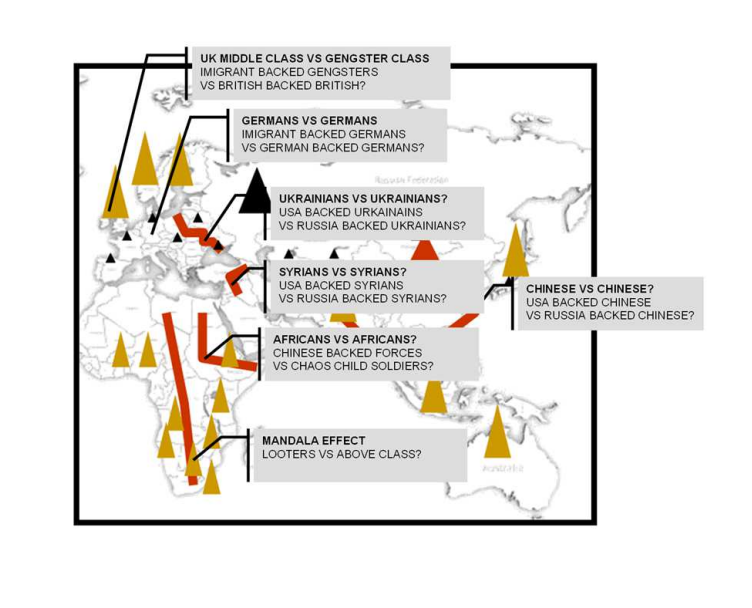
Sure, I can create ten short stories in English, Russian, and Hungarian based on your request. These stories will illustrate a family’s breakdown, focusing on themes such as infidelity, betrayal, and the cyclical nature of destructive behaviors. Each story will reflect the differences in sexual drives, nesting instincts, financial and emotional struggles, and other motivations. Here is the set of short stories in the three languages:
Story 1: The Collapse of Trust
English:
Maria cheated on Alex, and everything fell apart. He didn’t understand why she’d leave him for another man, as he’d always provided for her and their son. Maria, ashamed and seeking quick money, turned to prostitution. She gave her child to a stranger and moved into a world of survival. Her son grew up in an unstable environment and, just like his mother, turned to drugs to cope. The cycle of destruction continued.
Russian:
Мария изменила Алексу, и всё разрушилось. Он не понимал, почему она ушла к другому мужчине, ведь он всегда обеспечивал её и их сына. Мария, стыдясь и стремясь к быстрым деньгам, занялась проституцией. Она отдала своего сына чужому человеку и погрузилась в мир выживания. Её сын вырос в нестабильной среде и, как его мать, начал употреблять наркотики, чтобы справиться. Цикл разрушения продолжался.
Hungarian:
Mária megcsalta Alexet, és minden összeomlott. Alex nem értette, miért hagyta el őt egy másik férfiért, mikor mindig gondoskodott róla és a fiukról. Mária szégyenkezve, gyors pénzért prostitúcióra adta a fejét. Odaadta gyermekét egy idegennek, és belemerült a túlélés világába. A fia zűrös környezetben nőtt fel, és mint az anyja, drogokhoz nyúlt, hogy megbirkózzon a fájdalommal. A pusztulás ciklusa folytatódott.
Story 2: Breaking the Cycle
English:
Mia had no idea how deep her mistake was. She cheated on her husband, and he never truly forgave her. She sought solace in the streets, selling herself to strangers. Her child was placed in foster care, and as he grew, he became lost. Drugs, sex, and crime became his only way to feel alive. The vicious cycle of dysfunction never stopped.
Russian:
Миа не понимала, насколько глубока её ошибка. Она изменила мужу, и он так и не простил её. Она искала утешение на улицах, продавая себя чужим людям. Её ребёнка забрали в приёмную семью, и, подрастая, он терял себя. Наркотики, секс и преступления стали его единственным способом почувствовать жизнь. Замкнутый круг дисфункции не прекращался.
Hungarian:
Mia nem értette, mennyire mély a hibája. Megcsalta a férjét, és ő sosem bocsátott meg neki igazán. Vigasztalást keresett az utcákon, magát árulva idegeneknek. A gyermeke nevelőszülőkhöz került, és ahogy nőtt, elveszett. A drogok, a szex és a bűnözés lettek az egyetlen módjai, hogy életben érezze magát. A működőképtelen ciklus sosem állt meg.
Story 3: Desperate Measures
English:
Anna had always put the needs of others before her own, but when she cheated on her husband, she saw no way out. She became a prostitute to feed herself and her child. Her daughter, raised in neglect, began selling drugs to survive. The vicious cycle of dependence and destruction carried on through the generations.
Russian:
Анна всегда ставила чужие интересы выше своих, но когда она изменила мужу, она не увидела выхода. Она стала проституткой, чтобы прокормить себя и своего ребёнка. Её дочь, воспитанная в пренебрежении, начала продавать наркотики, чтобы выжить. Цикл зависимости и разрушения продолжался через поколения.
Hungarian:
Anna mindig mások szükségleteit tette előtérbe, de amikor megcsalta a férjét, nem látott kiutat. Prostituált lett, hogy eltartsa magát és gyermekét. A lánya, akit elhanyagoltak, drogot kezdett árulni a túlélés érdekében. A függőség és pusztulás ördögi köre generációkon át folytatódott.
Story 4: The Price of Pleasure
English:
Sofia knew she was using her body to escape pain, but she couldn’t stop. She’d betrayed her partner, and now she worked the streets. Her son, raised in a broken home, saw his mother’s actions as normal. He, too, sought pleasure in drugs, selling to others, just as his mother had sold herself.
Russian:
София понимала, что использует своё тело, чтобы убежать от боли, но не могла остановиться. Она предала своего партнёра, и теперь работала на улицах. Её сын, выросший в разрушенной семье, считал поступки матери нормой. Он тоже искал удовольствие в наркотиках, продавая их другим, как и его мать продавала себя.
Hungarian:
Szofia tudta, hogy a testét használja a fájdalom elkerülésére, de nem tudott megállni. Megcsalta a partnerét, és most az utcán dolgozott. A fia, aki egy szétesett családban nőtt fel, normálisnak látta édesanyja tetteit. Ő is a drogokban kereste az örömöt, és elkezdett árulni, ahogy édesanyja is eladta magát.
Story 5: The Illusion of Freedom
English:
Lena thought she could escape her pain by cheating, but instead, she entered a prison of her own making. She turned to prostitution and soon found herself trapped in a cycle of shame and guilt. Her daughter followed the same path, selling herself to survive. The family’s destruction seemed inevitable.
Russian:
Лена думала, что сможет убежать от своей боли, изменив, но вместо этого она оказалась в тюрьме, которую создала сама. Она пошла по пути проституции и вскоре оказалась в ловушке стыда и вины. Её дочь пошла тем же путём, продавая себя, чтобы выжить. Разрушение семьи казалось неизбежным.
Hungarian:
Léna azt hitte, hogy a megcsalással megszabadulhat a fájdalmától, de helyette egy saját maga által teremtett börtönbe került. Prostituált lett, és hamarosan szégyen és bűntudat fogságában találta magát. A lánya ugyanazon az úton indult el, hogy túléljen, eladva magát. A család pusztulása elkerülhetetlennek tűnt.
Story 6: Seeking Validation
English:
For Natalie, cheating was a cry for attention, but it led to a path of no return. She became a prostitute, hoping to find validation in the arms of strangers. Her son, never understanding his mother’s choices, fell into a world of crime and drugs. The pain continued through the generations.
Russian:
Для Натальи измена была криком о помощи, но это привело её на путь без возврата. Она стала проституткой, надеясь найти подтверждение своей ценности в объятиях чужих людей. Её сын, никогда не понимающий выбор матери, погрузился в мир преступности и наркотиков. Боль продолжалась через поколения.
Hungarian:
Natalie számára a megcsalás figyelemfelkeltés volt, de egy visszafordíthatatlan útra vezetett. Prostituált lett, remélve, hogy idegenek karjaiban talál megerősítést. A fia, aki sosem értette édesanyja választásait, a bűnözés és drogok világába süllyedt. A fájdalom generációkon keresztül folytatódott.
Certainly! Here are the next set of stories, continuing from the themes you’ve asked for:
Story 8: A Desperate Escape
English:
Mira thought she could escape her miserable life by cheating on her partner. But she only found herself deeper in despair, turning to prostitution. She abandoned her son, giving him to an orphanage. As he grew, he became a drug dealer, caught in a vicious cycle of addiction and crime. The pain, guilt, and desperation were passed on from one generation to the next.
Russian:
Мира думала, что сможет сбежать от своей несчастной жизни, изменив своему партнёру. Но она только углубила свою отчаянную ситуацию, став проституткой. Она оставила сына, отдав его в приют. Подрастая, он стал наркоторговцем, попав в порочный круг зависимости и преступности. Боль, вина и отчаяние передавались из поколения в поколение.
Hungarian:
Mira azt hitte, hogy megmenekülhet nyomorúságos életéből, ha megcsalja a partnerét. De csak egyre mélyebb kétségbeesésbe került, és prostituálttá vált. Elhagyta fiát, és egy árvaházba adta. Ahogy nőtt, drogkereskedő lett, és belekerült a szenvedélybetegség és bűnözés ördögi körébe. A fájdalom, bűntudat és kétségbeesés generációról generációra öröklődött.
Story 9: No Escape from Guilt
English:
After cheating on her husband, Claudia felt empty and alone. She tried to numb the pain by becoming a prostitute, but it only brought more guilt. Her son, who witnessed everything, ended up on the streets as well. He started dealing drugs to survive. His soul, like his mother’s, was broken beyond repair.
Russian:
После измены мужу, Клаудия почувствовала пустоту и одиночество. Она пыталась заглушить боль, став проституткой, но это принесло только больше вины. Её сын, ставший свидетелем всего, тоже оказался на улицах. Он начал торговать наркотиками, чтобы выжить. Его душа, как и у матери, была сломлена безвозвратно.
Hungarian:
Claudia, miután megcsalta a férjét, üresnek és magányosnak érezte magát. Megpróbálta elnyomni a fájdalmat prostituálttá válással, de ez csak még több bűntudatot hozott. A fia, aki mindent látott, ő is az utcára került. Drogokat kezdett árulni, hogy túléljen. A lelke, akárcsak az anyjáé, helyrehozhatatlanul összetört.
Story 10: The Broken Nest
English:
Vera always wanted a perfect family, but when she cheated on her husband, she destroyed everything. She turned to prostitution, hoping to fill the emptiness inside. Her daughter, now without a stable home, followed in her footsteps. She turned to selling herself and later to selling drugs. The cycle of destruction seemed endless as they all struggled with the need for financial survival and the pain of brokenness.
Russian:
Вера всегда хотела идеальную семью, но, изменив мужу, она разрушила всё. Она стала проституткой, надеясь заполнить пустоту внутри. Её дочь, теперь без стабильного дома, пошла по её стопам. Она начала продавать себя, а позже и наркотики. Цикл разрушения казался бесконечным, ведь все они боролись за финансовое выживание и страдали от разбитых жизней.
Hungarian:
Vera mindig is tökéletes családot akart, de amikor megcsalta a férjét, mindent tönkretett. Prostituálttá vált, remélve, hogy kitölti a belső ürességet. A lánya, aki már nem élt stabil otthonban, követte a nyomdokaiban. Először magát árulta, majd drogot kezdett árulni. A pusztulás ciklusa végtelennek tűnt, miközben mindannyian küzdöttek a pénzügyi túlélésért és a törött élet fájdalmával.
These stories reflect the destructive cycles that can emerge from broken relationships, highlighting themes of betrayal, generational pain, and the struggles with personal instincts versus societal expectations. They also explore the consequences of not understanding the deep emotional and biological differences in sexual drive and survival instincts, resulting in continuous suffering for both men and women within these families.
The Dance of Desire
Sophie and Ben had been living together for two years, their love as strong as the day they first met. But one thing always puzzled Sophie—how different their sexual drives seemed to be. Sophie, with her 28-day cycle, noticed that her libido ebbed and flowed, while Ben, it seemed, was always ready for intimacy. As time passed, these differences became more apparent.
One evening, after a particularly long day of work, Sophie collapsed onto the couch. Ben, always affectionate, wrapped his arms around her, whispering sweetly in her ear. Sophie smiled but couldn’t help feeling a wave of exhaustion. Tonight’s not the night, she thought. She leaned back into him, but her body wasn’t craving the closeness she once did. Ben, on the other hand, seemed eager and initiated another round of cuddling, followed by playful touches. Sophie sighed, gently pulling away.
“I’m just not in the mood tonight,” she explained, her voice soft yet firm.
Ben blinked in confusion. “But I thought we were close. Is something wrong?”
Sophie hesitated, realizing the truth of the situation. She had explained to Ben before that her sexual drive wasn’t a daily affair like his. Her body followed a rhythm, a cycle of highs and lows, shifting throughout the month. She remembered a conversation they’d had months ago, when she tried to explain her 28-day hormonal cycle and how it influenced her libido.
Ben, though understanding, sometimes struggled with the differences between them.
“Maybe you’re right,” Sophie said. “It’s just that I’m not feeling the same way tonight. Tomorrow, maybe.”
Ben smiled, though there was a hint of disappointment. “I get it. It’s just… hard for me to understand sometimes.”
Sophie smiled back, appreciating his patience. But she knew there were differences that could sometimes cause tension between them. As she looked back over their time together, she reflected on the seven key differences that their cycles brought into their relationship:
- The Hormonal Cycle vs. The Daily Drive
Sophie’s libido naturally fluctuated in line with her 28-day hormonal cycle. On some days, she felt a surge of desire, while other days were slower and less intimate. Ben, however, had a more constant drive, experiencing daily peaks of sexual energy that didn’t wane as dramatically. This sometimes created a mismatch, especially when Sophie was in the quieter phase of her cycle.
- Emotional Connection vs. Physical Urge
Sophie often craved a deeper emotional connection before engaging in physical intimacy. During her fertile phase, she felt more drawn to Ben, emotionally and physically. Ben, on the other hand, felt more driven by the physical aspect of sex and didn’t always need the same emotional build-up. This difference sometimes led to misunderstandings about what each partner needed in the moment.
- Desire Peaks
During ovulation, Sophie’s desire surged, and she often found herself initiating intimacy. But for Ben, his desire didn’t follow a monthly rhythm—it was steady. This timing mismatch meant that Sophie sometimes felt more desire when Ben didn’t, and vice versa. When Sophie was at her peak, Ben might already have had his own emotional or physical needs satisfied earlier in the cycle.
- The Impact of Stress
Sophie noticed that her libido was often affected by stress—work, life pressures, and even her hormonal changes. When she was stressed, her desire often decreased, and intimacy took a back seat. Ben, however, was less affected by stress and could be ready for intimacy even after a long, stressful day. This difference sometimes led to Sophie feeling pressure when Ben was more persistent.
- Physical Changes
Sophie’s body went through subtle physical changes throughout her cycle—her breasts felt more sensitive during ovulation, and her energy levels fluctuated. These natural changes influenced her sexual interest. Ben, however, didn’t experience the same physical shifts and often wondered why Sophie’s sexual drive wasn’t as consistent as his.
- Receptivity to Touch
Sophie’s sensitivity to touch varied throughout her cycle. During certain times, she was more touchy and affectionate, while other times, physical contact felt overwhelming. Ben, on the other hand, tended to respond to touch consistently, which sometimes left Sophie feeling guilty when she wasn’t as physically affectionate.
- Frequency and Intensity
Sophie didn’t need daily sex to feel connected or loved. Her desire for intimacy was more spread out, often peaking during certain points in her cycle. Ben, however, wanted a more frequent connection, and sometimes his daily sexual drive left Sophie feeling pressured to meet his expectations, even when she wasn’t in the mood.
Despite these differences, Sophie and Ben’s love was strong. They had learned to communicate openly about their needs and boundaries, understanding that the rhythms of their bodies were as much a part of who they were as their personalities. Over time, Sophie found ways to express her feelings in a way that Ben could understand, and Ben learned to be patient, allowing Sophie the space to experience her desires on her own terms. Their relationship thrived because they embraced their differences, using them as an opportunity for deeper connection and understanding.
And so, Sophie and Ben’s journey continued—a dance of desire, respect, and love, with each step guided by their unique rhythms.